 Satendra K
Apr 23, 2025
Satendra K
Apr 23, 2025
A cyberattack is the unauthorized breach of systems and software intended to cause significant harm and damage to individuals or organizations. Cybercriminals use various techniques, including malware, phishing, and ransomware, to initiate a cyberattack. The motivations behind cyber attacks can vary significantly. Generally, there are three primary types of motivations: criminal, personal, and political.
Attackers with criminal intent aim to profit financially through activities such as data theft, stealing money, or disrupting business operations. On the other hand, individuals who are personally motivated, such as disgruntled current or former employees, may steal money or data, or seek to disrupt a business's systems out of a desire for revenge. Political attackers, meanwhile, seek to draw attention to their issues and often publicise their actions.
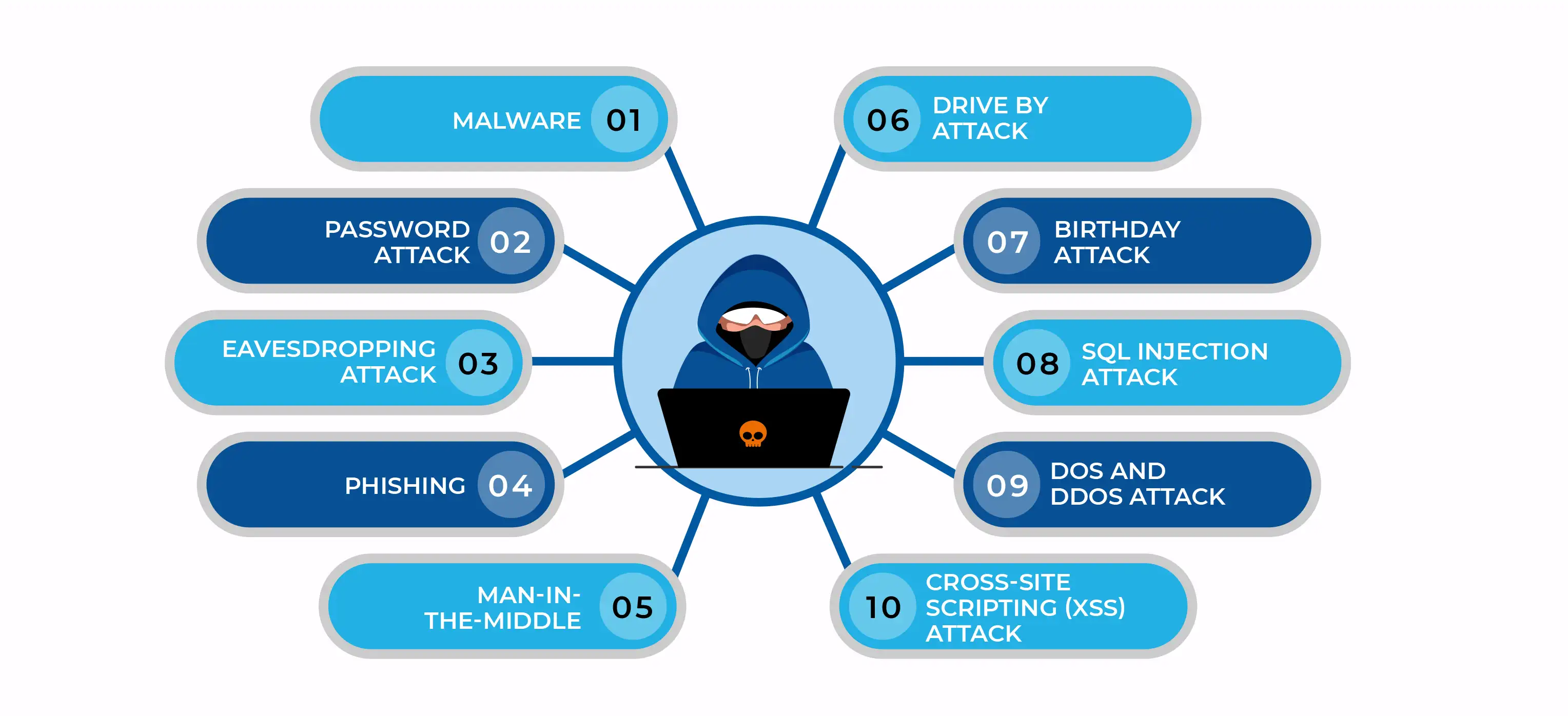
The cases of cyberattacks are rising globally with each passing year. Let’s dive deep into the top 10 most common types of cyberattacks,
Malware, also known as malicious software, is an unwanted software that has been installed on your computer against your will to harm computer systems/networks. It can duplicate itself on the Internet, hide in helpful apps, and attach itself to genuine code to spread. Here are a few of the most typical malware varieties;
A password attack is a type of cyberattack where an attacker attempts to gain unauthorized access to a system through a user’s password. Obtaining passwords is a widespread and efficient attack strategy since passwords serve as the most popular method of user authentication for information systems. By tricking users into revealing their passwords through fake websites or spam emails, employing social engineering, connecting to a password database, or just guessing, attackers can crack the password.
A brute-force password attack involves using every combination of characters by the attacker until the right password is found. The attacker employs a random strategy by attempting various passwords in the hopes that one will be successful. By testing passwords based on the person's name, occupation, interests, or other comparable factors, attackers attempt to crack the password.
A dictionary attack is a type of brute-force attack where a dictionary of popular passwords is used to access a user's computer and network. One common method used by attackers is copying a password-containing encrypted file, using the same encryption on a dictionary of passwords that are often used, and evaluating the results. Implementing an account lockout policy that locks the account after a few unsuccessful password tries will help you defend against dictionary or brute-force assaults.
Read Also : Top Cybersecurity Training Companies in Sydney, Australia
An eavesdropping attack is a type of security breach where the attacker intercepts network traffic and obtains passwords, login credentials, credit card numbers, and other private information that a user may be communicating over the network. Cybersecurity awareness courses will help you gain in-depth knowledge on how to protect yourself from such attacks.
A passive eavesdropping is done by the hacker by silently monitoring the network's message traffic/ communication channel without making any alterations. In active eavesdropping, hackers deliberately steal information by posing as friendly units, sending inquiries to transmitters, and by other means. This is similar to tampering, scanning, or probing, a Man-in-the-Middle Attack.
Phishing is a form of cyberattack where the attacker sends emails that look like they are from a reliable source to get users' personal information. It can entail downloading malware onto your machine through an email attachment or SMS. You might be tricked into installing malware or providing your personal information by clicking on a link to a dubious website. There are various types of Phishing
A Man-in-the-Middle (MitM) is a type of malicious attack where the attacker intercepts through unsecured Wifi or compromised routers and possibly alters the communication between two parties. MitM attacks could result in data breaches, identity theft, or financial loss. Email hijacking and HTTP spoofing are some of the common types of MitM attacks. An ethical hacker with advanced hacking skills can tackle these kinds of attacks.
A drive-by attack is a type of cyberattack that targets insecure websites by inserting harmful scripts into their PHP code. Visitors to the website could either be redirected to a site run by hackers or have malware installed directly onto their computers by this script. Drive-by downloads can occur when a user views a pop-up window, an email, or a website. The attacker can gain full control of the user’s system, leading to credential theft and the opening of backdoors for further attacks.
The future of cybersecurity is characterized by increased reliance on automation. According to Mark London, President of Verity IT, “AI-powered threat-intelligence platforms will be the most in-demand cybersecurity tool in the future. As cyber threats continue to evolve, AI-driven threat intelligence tools will be essential for businesses to stay ahead of attackers and protect their critical assets.”
A birthday attack is a type of cryptographic attack where the attacker uses probability theory and the birthday paradox. The integrity of a message, piece of software, or digital signature is checked using hash algorithms. Birthday attacks are made against these hash algorithms. When a message is analyzed by a hash function, a message digest (MD) is generated that is a fixed length and independent of the length of the original message. This MD uniquely identifies the message.
The birthday attack is a term used to describe the likelihood of discovering two messages that produce the same MD after being analyzed by a hash function. The attacker can simply replace the user's message with his own if he calculates the same MD for it as the user has, and the recipient won't be able to tell the difference, even if they analyze MDs. Stringent cybersecurity measures can avoid these types of attacks.
SQL injection is the placement of malicious code in SQL statements by the attacker. Database-driven websites now frequently experience SQL injection problems. These attacks happen when a malicious party uses the supplied information provided by the client to the server to perform a SQL query on the database. Through SQL injection, a hacker can obtain sensitive data from the database, edit database data, run administration activities on the database, retrieve the information of a provided file, and, in some situations, give orders to the operating system.
The Distributed Denial of Service (DDoS) is a cyberattack where bots are used to flood a targeted website or server with traffic, making it unavailable to the actual user. The resources of a system are overloaded during a denial-of-service attack, making it unable to react to service requests. A DDoS attack targets a system's resources as well, but it does so from a huge number of additional host computers that have been infected with malicious software that is under the attacker's control.
The Denial of Service (DoS) attack is an attempt to disrupt or completely stop the normal functioning of the server or network service by flooding it with illegitimate requests. The DoS attack causes the target to become slow or unresponsive, eventually leading to a website crash, data breach, or financial crash. Such attacks might not directly benefit the attacker. The pleasure of service denial is sufficient for some of them. The gain to the attacker, however, can be sufficient if the resource is owned by a rival company. A DoS attack may also be used to knock a system down so that another assault can be started. Upskilling the cybersecurity team equips the organization to combat these advanced-level cyberattacks.
Cross-site scripting (XSS) attacks leverage third-party online resources to launch scripts in the scriptable application or web browser of the victim. The attacker specifically inserts a payload containing JavaScript into a website's database. The website sends the victim's browser the malicious script-containing page when the user asks for a page from the site, which includes the attacker's payload as a component of the HTML body. Stored XSS, Reflected XSS, and DOM-based XSS are some of the types of Cross-Site Scripting attacks.
The digital transformation of society has escalated the cyberattacks at an alarming rate, affecting individuals, governments, and small and large organizations alike. Various interconnected factors have given rise to cyberattacks, such as technological advancement, global connectivity, a lack of cyber awareness, and a skill gap in cybersecurity. The increasing cases of cybercrime can be combated by increasing public awareness of cybersecurity, investing in cybersecurity research, and strengthening international collaboration to fight cybercrime.
Here is the list of other major locations where Edoxi offers Cyber Security Courses
Cyber Security Courses in Dubai | Cyber Security Courses in Qatar | Cyber Security Courses in Muscat|Cyber Security Courses in Bahrain | Cyber Security Courses in Riyadh | Cyber Security Courses in Kuwait | Cyber Security Courses in Muscat |

Chief Technology Officer & Cyber Security Expert Trainer
Satendra Singh Khari is a renowned cybersecurity expert and the Chief Technology Officer at Edoxi, where he leads the CEH v13 AI program. With over 12 years of experience, he has trained more than 10,000 professionals and earned recognition in the Circle of Excellence for 2023 and 2024. Mr. Khari holds multiple industry certifications, including CISSP, CISM, CEH, CPENT, and CREST, which showcase his expertise in vulnerability assessment, penetration testing, and incident handling.
His practical insights, gained during his tenure as Head of Information Security in Malaysia, enhance the learning experience by providing students with essential technical skills and a clear path to career advancement. Recognized as a leader in his field, he has received the Internet 2.0 Outstanding Leadership Award for three consecutive years (2022-2024), reflecting his dedication to empowering the next generation of cybersecurity professionals.