Edoxi Training Institute is an EC-Council-accredited training center, delivering a 40-hour Certified Network Defender (C|ND) v3 course in Dubai. This course is designed to help IT professionals build strong network defence skills and develop a security-first mindset. It is ideal for individuals who want to begin or advance their careers in cybersecurity, especially in blue team operations.
The Certified Network Defender (C|ND) v3 is a globally recognised certification from the EC-Council. Our C|ND course includes full exam preparation aligned with the official EC-Council C|ND v3 certification. It covers essential topics such as network security fundamentals, system security, disaster recovery, and threat intelligence. You will gain practical experience through our hands-on labs using live target machines. This network security course serves as an ideal pathway to begin a cybersecurity career, particularly in blue team operations.
Edoxi’s CND Course is available in both classroom and online formats, with flexible schedules to suit both individuals and corporate teams. For businesses, we offer a customised 5-day corporate training that can be delivered at a selected hotel, client premises or Edoxi. The training focuses on developing the skills needed to prevent, detect, respond to, and recover from cyberattacks. It follows a 4-pronged adaptive security strategy, helping professionals understand and apply real-world defensive techniques.
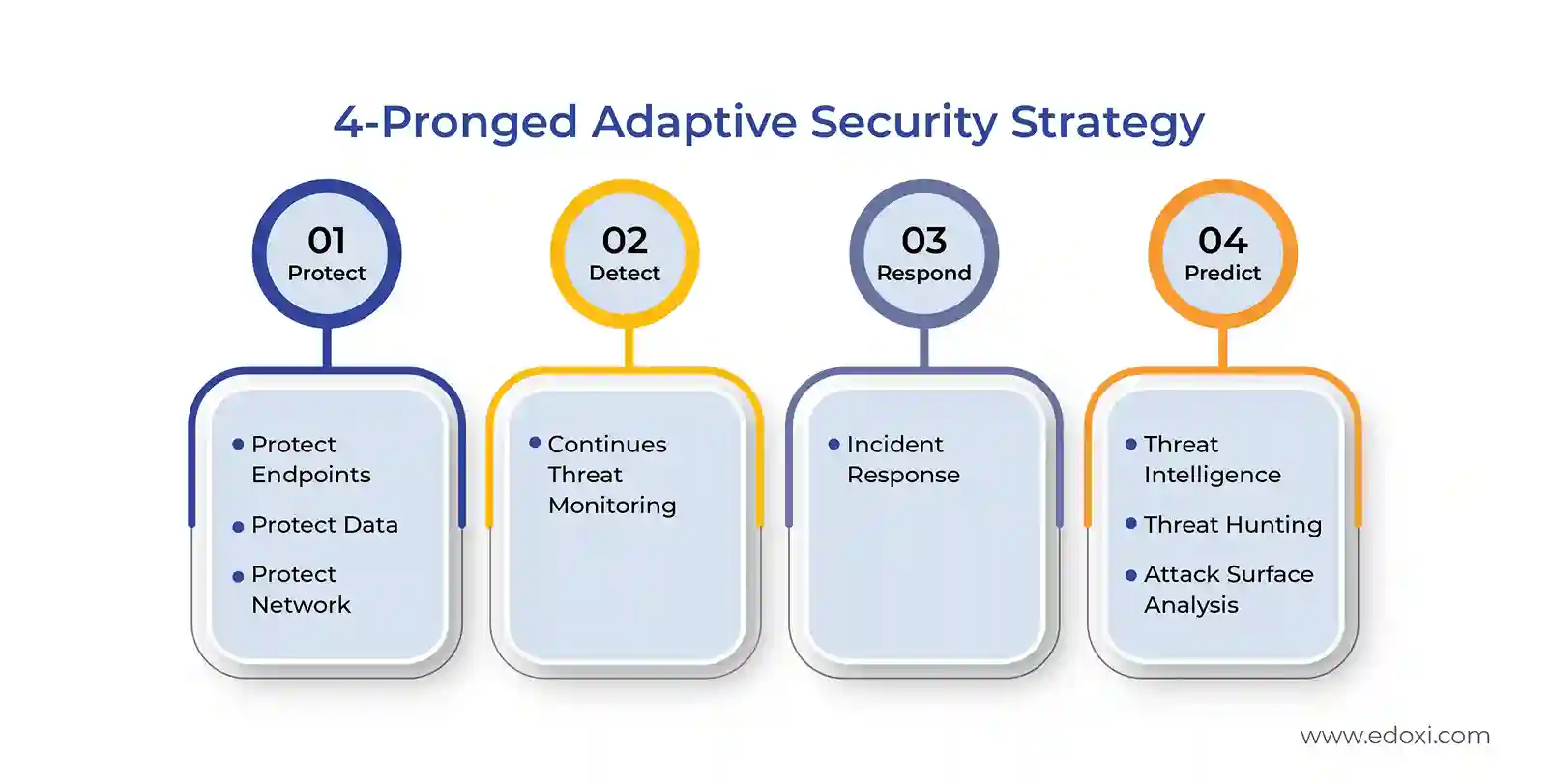
Our C|ND training builds robust network security capabilities. The course is specifically tailored to build advanced network security capabilities for today’s threat landscape. It prepares defenders with the strategic, technological, and operational skills to design, develop, and maintain secure networks across diverse environments.
Train with Edoxi and start your journey toward a successful cybersecurity career in Dubai.
| Exam Criteria | Details |
| Exam Name | Certified Network Defender (C|ND) |
| Duration | 4 hours |
| Number of Questions | 100, Multiple Choice |
| Passing Score | 60%-80% (depending on question weightage) |
| Certification Validity | 3 Years |
| Exam Administration Authority | EC-Council |
You’ll practice in a dedicated cloud environment designed specifically for cybersecurity hands-on activities.
Get access to comprehensive study materials created by the certification authority with up-to-date network defence concepts.
Participate in specialised training exercises tailored to different network security roles and responsibilities.
Learn to defend against simulated network, application, and host-based attacks using industry-standard security tools.
Master skills to configure and deploy firewall, IDS/IPS solutions using pfSense, Suricata, and Wazuh in hands-on laboratory sessions.
You’ll engage in practical threat-hunting activities focusing on indicators of compromise and attack surface analysis.
IT professionals managing network infrastructure who need to implement and maintain security controls across enterprise environments.
Cybersecurity team members are responsible for monitoring networks, detecting threats, and implementing defensive measures.
IT administrators seeking to enhance their security skill set with specialised knowledge in protecting network resources.
Technology specialists are looking to develop defensive security skills and move into dedicated network security roles.
Individuals with foundational cybersecurity knowledge are ready to specialise in network defence methodologies.
Security professionals are responsible for developing and enforcing network security policies and procedures.
Edoxi’s Certified Network Defender course in Dubai offers dedicated cloud-based practice labs. These labs feature real-world cybersecurity simulations and tactical defence exercises. Classroom activities include case studies and role-based security training utilising EC-Council's accredited cybersecurity lab environment for hands-on skill development. This course covers the following key activities.
Analyse complete network breach scenarios with detailed walkthroughs of detection methodologies, response procedures, and recovery processes based on real-world security incidents.
Participate in simulated network, application, and host-based attacks while implementing appropriate defence strategies and countermeasures.
Configure identity and access management, security policies, asset management, cryptography, VPNs, and network segmentation.
Configure and deploy firewall protection and intrusion detection/prevention systems using pfSense, Suricata, and Wazuh to secure network boundaries.
Implement comprehensive security for Windows, Linux, mobile, and IoT devices through OS hardening, patching, encryption, file integrity, and permissions management.
Design and implement security controls for virtual machines, containers, and cloud environments, including IAM configurations for AWS, Azure, GCP, KMS, storage, and network overlays.
Configure router and Wi-Fi encryption and authentication to secure wireless network communications against unauthorised access.
Perform packet capture, establish Wireshark baselines, and conduct traffic and log analysis to identify security anomalies.
Develop and execute incident response plans, conduct forensic investigations, and implement disaster recovery exercises for business continuity.
Edoxi’s Certified Network Defender course in Dubai provides a structured career path for the UAE’s cybersecurity defence sector. These cybersecurity job roles offer excellent growth potential and opportunities to work in organisations prioritising network security across critical infrastructure. The following are some of the outcomes that you can expect after completing our course in Dubai;

Get expert assistance in getting your CND Course customised!
Here’s a four-step guide to becoming a certified CND professional.
Join Edoxi’s CND Course
Here are a few reasons why you should choose Edoxi for Certified Network Defender Training in Dubai;
We are an EC-Council authorised training partner, delivering exceptional training and outstanding outcomes in cybersecurity education in the UAE region.
Our structured curriculum, expert instruction, and extensive practice labs will prepare you for success in the Certified Network Defender exam.
You get to practice in EC-Council's accredited cloud lab featuring real-world network infrastructure, attack scenarios, and industry-standard security tools for comprehensive hands-on learning.
We follow EC-Council's official curriculum, enhanced with supplementary resources, practical defence exercises, and personalised guidance from experienced security professionals.
Join hundreds of successfully trained and certified network security professionals who have advanced their careers through our established cybersecurity training programs.
Get access to a full spectrum of complementary cybersecurity courses, including CEH, CHFI, and ECSS, creating a comprehensive professional development roadmap for your security career.

Our mentors are leaders and experts in their fields. They can challenge and guide you on your road to success!

Satendra K
Satendra Singh Khari is a renowned cybersecurity expert and the Chief Technology Officer at Edoxi, where he leads the CEH v13 AI program. With over 12 years of experience, he has trained more than 10,000 professionals and earned recognition in the Circle of Excellence for 2023 and 2024. Mr. Khari holds multiple industry certifications, including CISSP, CISM, CEH, CPENT, and CREST, which showcase his expertise in vulnerability assessment, penetration testing, and incident handling.
His practical insights, gained during his tenure as Head of Information Security in Malaysia, enhance the learning experience by providing students with essential technical skills and a clear path to career advancement. Recognized as a leader in his field, he has received the Internet 2.0 Outstanding Leadership Award for three consecutive years (2022-2024), reflecting his dedication to empowering the next generation of cybersecurity professionals.
Here is the list of other major locations where Edoxi offers CND Course