Edoxi’s EC-Council–authorised Digital Forensic Essentials Course in Dubai strengthen your cybersecurity career. The Course helps you master key areas such as forensic imaging, data recovery, and evidence collection. Our curriculum is designed for IT professionals, cybersecurity enthusiasts, and career changers who want to gain practical knowledge in cybercrime investigation and digital evidence handling.
This Digital Forensic Essentials Course in Dubai develop practical skills required to collect, analyse, and preserve digital evidence in real-world investigations. Learners train using leading digital forensic tools such as Autopsy and Wireshark. Through guided, tool-based sessions, you’ll perform tasks like disk cloning, file system analysis, and email header investigation.
The course focuses on chain of custody procedures to ensure digital evidence is handled correctly throughout an investigation. Participants gain insight into the ethical and legal aspects of digital forensics, which are essential for professionals working in law enforcement, compliance, and corporate investigations.
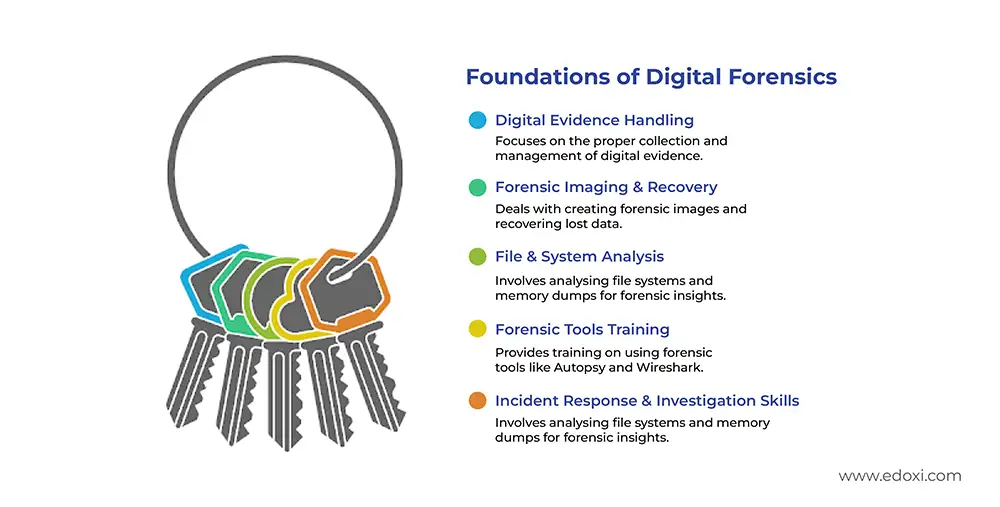
Dubai’s growing need for cybersecurity and digital investigation specialists has made digital forensics skills one of the most sought-after in the UAE job market. Certified professionals enjoy higher salaries, career advancement opportunities, and roles in government, finance, and corporate sectors. Organisations also benefit as employees learn to perform incident response, memory dump analysis, and Windows Registry forensics. These skills help reduce security risks, improve investigation efficiency, and ensure regulatory compliance.
Enrol now and gain the technical expertise, certification, and confidence to pursue roles such as Digital Forensic Analyst, Cybersecurity Investigator, or Incident Response Specialist in Dubai and across the UAE.
Digital Forensic Essentials (DFE) Exam Details:
Our curriculum aligns with EC-Council's certification exam objectives, preparing students to successfully pass the 112-57 Digital Forensics Essentials (DFE) certification exam. Key details of the exam;
| Exam Criteria | Details |
| Exam Code | 112-57 |
| Exam Name |
EC-Council Digital Forensics Essentials
|
| Duration | 2 hours |
| Number of Questions | 75, Multiple Choice |
| Passing Score | 70% |
| Certification Validity | 3-years |
| Exam Administration Authority | EC-Council |
Practice in a specialised lab setup with forensic workstations and professional-grade tools like Autopsy and Wireshark.
Work through authentic case studies involving compromised systems, deleted evidence recovery, and network attack analysis.
Receive targeted preparation for the 112-57 Digital Forensics Essential (DFE) certification exam with practice questions and scenario-based assessments.
Examine file systems practically to understand metadata, timestamps, and deleted file recovery using forensic techniques.
Analyse network communications with Wireshark to identify suspicious activities and trace digital evidence across networks.
Utilise industry-standard templates for maintaining the chain of custody and producing court-admissible investigation reports.
Technical specialists seeking to expand into cybersecurity incident investigation roles.
Students and graduates pursuing careers in digital forensics and security.
Officers needing digital evidence collection skills for modern investigations.
IT admins adding forensic capabilities to enhance security incident management.
Organisations building in-house capabilities for preliminary digital investigations.
Professionals transitioning to cybersecurity roles starting with forensic fundamentals.
This course offers extensive hands-on labs focusing on digital evidence collection and forensic analysis techniques. Classroom activities include simulated investigations using professional tools like Autopsy and Wireshark.
Retrieve intentionally deleted evidence using file carving techniques while maintaining proper chain of custody documentation.
Create forensically sound disk images using the dd command and verify integrity through multiple hash functions.
Use cryptographic functions to verify evidence integrity and establish non-repudiation for collected digital artefacts.
Extract data fragments from solid-state drives despite TRIM commands that complicate traditional recovery methods.
Analyse network traffic to identify suspicious patterns, malicious connections, and evidence of intrusion attempts.
Examine email headers, attachment metadata, and embedded links to trace origins and identify phishing attempts.
Analyse potentially malicious files without execution to identify indicators of compromise and malware characteristics.
Identify artefacts indicating TOR usage and recover browsing evidence despite anonymisation attempts.
Edoxi’s Digital Forensic Essentials course in Dubai opens doors to numerous job roles in Dubai's digital investigation field. Completing the Digital Forensic Essentials course offers measurable benefits to organisations, including:

Get expert assistance in getting you Digital Forensic Essentials (DFE) Course customised!
Here’s a four-step guide to becoming a certified Digital Forensic Essentials professional.
Join Edoxi’s Digital Forensic Essentials (DFE) Course
Edoxi is a leading training institute offering EC-Council Accredited courses in Dubai. The following are some of the reasons why you should choose Edoxi for your training needs;
Official partnership ensures curriculum meets EC-Council's global standards for digital forensics certification.
Instructors with extensive industry experience in cybersecurity investigations and forensic analysis techniques.
Professional forensic exercises with industry-standard tools like Autopsy and Wireshark for practical learning.
Edoxi offer clear progression from foundational courses to advanced certifications, building a comprehensive cybersecurity skillset.
Limited batch sizes ensure personalised attention and thorough coverage of complex digital forensic concepts.
We deliver customised training to government bodies, banks, and enterprises across the UAE and the Middle East.

Our mentors are leaders and experts in their fields. They can challenge and guide you on your road to success!

Maria Mehwish
Maria Mehwish is a forward-thinking and knowledgeable information security leader with a strong background in building, updating, and maintaining digital protections for various organisations. As a certified CEH, CCSP, CCT, and CISSP Trainer, Maria has a proven track record of delivering innovative and immersive coursework, enhancing learning experiences for cyber threats, ethical hacking, security policy, DevSecOps, and cloud security. With excellent verbal and written communication skills, she is also adept at troubleshooting problems and building successful solutions.
Maria is a self-motivated individual with a strong sense of personal responsibility, capable of managing projects from start to finish. Her expertise in Amazon Web Services, Java/Go/Python/C++, DevSecOps, computer security, Linux, penetration testing, and risk analysis, among others, makes her a valuable asset to any organisation. Maria, a British national, is a native English speaker and has intermediate proficiency in Urdu.
Yes, the Digital Forensic Essentials course is specifically designed as an entry point for beginners. It introduces fundamental concepts and builds technical skills progressively through hands-on exercises.
There are no formal prerequisites needed to join Edoxi’s Digital Forensic Essentials (DFE) Course in Dubai. This makes it accessible to beginners in digital forensics.
Graduates can apply for entry-level positions such as Digital Forensics Assistant, SOC Analyst, or Cybersecurity Technician in various sectors, including financial institutions, law enforcement, and corporate security teams.
Organisations benefit from improved internal incident response capabilities, proper evidence handling procedures, and preliminary investigation skills that can significantly reduce security incident costs and compliance risks.
The certification is valid for three years from the date of passing the exam. After this period, you can recertify by taking the exam again to maintain your credentials.