Edoxi’s 30-hour CISSP Course in Sydney, Australia is built for professionals who want to earn one of the most respected certifications in cybersecurity. Delivered fully online, our Certified Information Systems Security Professional (CISSP) course gives you the flexibility to fit study around your work and lifestyle. You cover all eight CISSP domains and gain the skills to design, manage, and secure enterprise systems in line with global security standards.
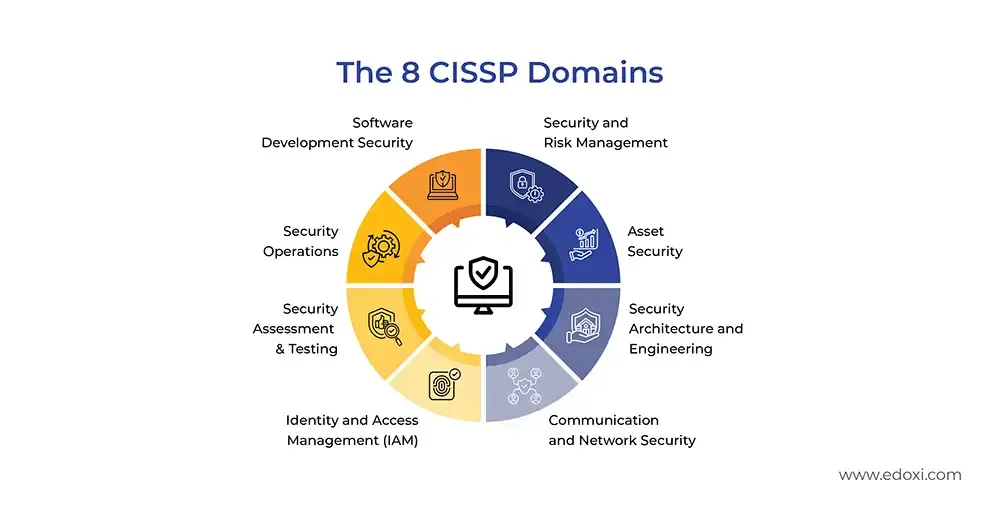
Our CISSP training in Sydney blends theory with practice. Through interactive online labs and real-world simulations, you work with industry tools such as Nmap, Wireshark, and Metasploit. You learn how to run vulnerability assessments, strengthen security architecture, and apply proven strategies to protect business-critical data. This hands-on focus means you build the confidence to use CISSP knowledge in your current role while preparing for the exam.
CISSP Exam Details
| Exam Criteria | Details |
| Exam Name | Certified Information Systems Security Professional (CISSP) |
| Exam Duration | 3 hours (Computerised Adaptive Testing) |
| Question Format | 100-150 questions, including MCQs and advanced innovative items |
| Passing Score | 700 out of 1000 points |
| Exam Fee | USD 749 |
| Certification Validity | 3 Years |
| Exam Authority | ISC2 Authorized PPC and PVTC Select Pearson VUE Testing Centers |
The CISSP certification exam, run by ISC2 through Pearson VUE testing centres, is a 3-hour Computerised Adaptive Test with 100–150 questions that include multiple-choice and scenario-based items. To pass, you need a score of at least 700 out of 1000. The standard exam fee is USD 749. Once certified, your credential is valid for three years. To stay certified, you need to remain active in one of the CISSP domains, show proof of ongoing security practice, and follow ISC2’s Code of Professional Ethics. This ensures your skills remain current and recognised worldwide.
By completing Edoxi’s online CISSP course, you position yourself for career growth and international recognition. As a CISSP-certified professional, you open the door to roles such as Security Analyst, Security Manager, or even Chief Information Officer. With the rising demand for cybersecurity experts and attractive salary packages, the CISSP certification gives you the credibility and competitive edge to lead and protect in today’s digital-first world.
You access pre-configured online labs that cover all CISSP domains. You practise real-world vulnerabilities and security scenarios in a safe, hands-on environment.
You gain experience with industry tools such as Kali Linux for security testing, OpenVAS for vulnerability assessment, and Snort for intrusion detection.
You take part in group discussions and problem-solving sessions. You work on real-world challenges across all eight CISSP domains with a focus on practical application.
You use the official ISC2 CISSP book and presentation materials. You strengthen your preparation with practice questions and domain-specific mock exams.
You perform vulnerability scanning, penetration testing, and detailed security assessments. You apply industry-standard methods that match CISSP exam objectives.
You complete structured exercises after each domain module. You focus on essential skills such as policy development, risk assessment, and incident response planning.
If you are an experienced IT professional aiming to strengthen your cybersecurity expertise with ISC2’s globally recognised CISSP certification, this course supports your role in managing enterprise security initiatives.
If you are an infrastructure specialist responsible for security architecture and implementation, this training helps you expand your security management skills.
If you are a practising security consultant or analyst, this course validates your expertise and prepares you for more senior-level positions.
If you are an engineer managing secure communication infrastructures, this program enables you to master enterprise-wide security solutions and advanced architectures.
If you are a professional overseeing compliance frameworks and asset protection, this training enhances your strategic governance and risk management capabilities.
If you are an individual with a solid IT foundation and a passion for cybersecurity, this course gives you the platform to pursue a long-term career in the field.
Our CISSP course combines hands-on labs and real-world exercises to help you apply your learning practically and confidently. Each activity is designed to reinforce key skills across all CISSP domains. Our labs and practical sessions include:
You have access to pre-configured labs for each CISSP domain. You can practise security tasks in a controlled setting using step-by-step instructions.
You learn to use essential security tools like Kali Linux for testing, OpenVAS for vulnerability scanning, and Snort for intrusion detection. You gain practical skills that apply to real-world security environments.
You learn to develop comprehensive security policies tailored to organisational needs. You learn to implement frameworks and enforce security controls effectively.
Conduct vulnerability assessments and simulated penetration tests. You apply real-world testing techniques to identify and mitigate security risks.
You learn to create practical incident response plans for various scenarios. You learn to handle security incidents efficiently, from detection to mitigation.
You learn to perform detailed risk assessments for critical IT systems. You apply course principles to evaluate threats and design risk management strategies.
During our CISSP Course, you can boost your cybersecurity expertise and prepare for a globally recognised CISSP certification. You gain the knowledge and practical skills to design, implement, and manage robust security solutions across enterprises.

Get expert assistance in getting you CISSP Course customised!
Here’s a four-step guide to becoming a certified CISSP professional.
Join Edoxi’s CISSP Course
At Edoxi, we bring you a CISSP Certification Training program in Sydney designed to meet the needs of IT security professionals, administrators, consultants, and managers. Our focus is on giving you the right knowledge, skills, and confidence to achieve one of the world’s most respected cybersecurity credentials. Here are the reasons to choose us for your CISSP Training.
Our CISSP-certified instructors are industry experts with advanced security qualifications and years of teaching experience. We guide you through practical, industry-focused training that prepares you for real-world challenges.
We keep our batches small so you get individual attention. You gain access to our web-based labs with real-world security scenarios and our curriculum stays fully aligned with the latest ISC2 requirements.
We support you at every step, from registration to documentation. You receive our guidance on endorsement requirements and eligibility verification so that your certification journey is smooth.
You practise in our domain-specific labs using tools like Kali Linux, OpenVAS, and Snort. We help you perform vulnerability assessments, penetration testing, and security implementation tasks that sharpen your skills.
We provide classroom, online, and corporate training options. You benefit from flexible schedules, intensive 5-day corporate programs, and recorded sessions for online learners so you can learn at your own pace.
We design our course to enhance your employability. You gain practical skills and insights that make you stand out to top employers in Sydney’s growing cybersecurity industry.

Our mentors are leaders and experts in their fields. They can challenge and guide you on your road to success!

Maria Mehwish
Maria Mehwish is a forward-thinking and knowledgeable information security leader with a strong background in building, updating, and maintaining digital protections for various organisations. As a certified CEH, CCSP, CCT, and CISSP Trainer, Maria has a proven track record of delivering innovative and immersive coursework, enhancing learning experiences for cyber threats, ethical hacking, security policy, DevSecOps, and cloud security. With excellent verbal and written communication skills, she is also adept at troubleshooting problems and building successful solutions.
Maria is a self-motivated individual with a strong sense of personal responsibility, capable of managing projects from start to finish. Her expertise in Amazon Web Services, Java/Go/Python/C++, DevSecOps, computer security, Linux, penetration testing, and risk analysis, among others, makes her a valuable asset to any organisation. Maria, a British national, is a native English speaker and has intermediate proficiency in Urdu.
Here is the list of other major locations where Edoxi offers CISSP Course