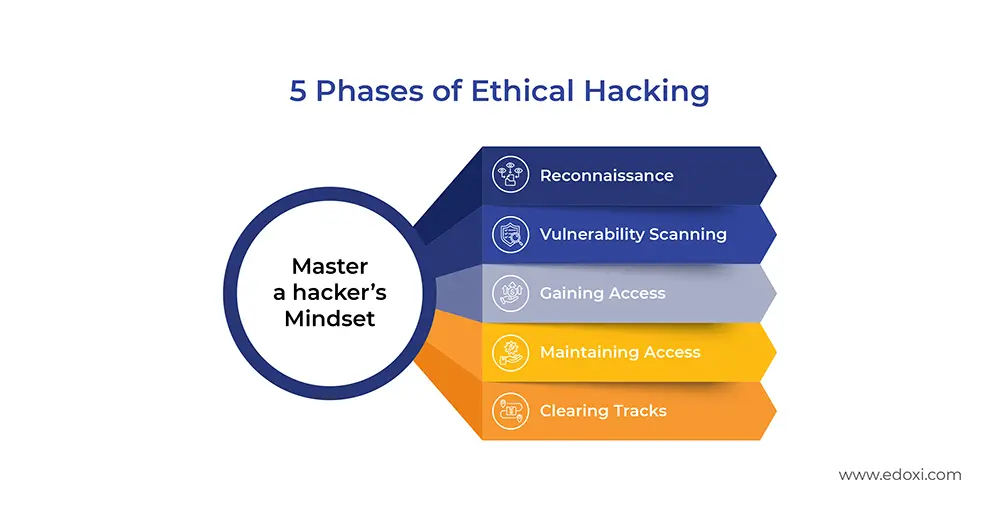
Certified Ethical Hacker v13 is the world’s first ethical hacking program powered by AI and was introduced by the EC Council. Certified Ethical Hacker (CEH v13) Course offers comprehensive hands-on training and fosters a hacker's mindset by integrating AI into all five phases of ethical hacking, including:
Join the AI Revolution as a Certified Ethical Hacker in Version 13 with Edoxi Training Institute in Dubai, an EC Council Approved Training Center for Cybersecurity Courses. Edoxi has also secured EC-Council ATC of the Year Awards in 2023 and 2024.
Edoxi will help you gain expertise to navigate the cutting-edge world of cybersecurity as a Certified Ethical Hacker, trained in the latest version of CEH v13 powered by AI.
Our industry-experienced and certified cyber security trainers will help you to equip you with AI-powered tools and techniques to identify, exploit, and secure vulnerabilities in systems and networks.
Our CEH v13 AI Course guided by our cybersecurity experts will help you:
Our training integrates advanced AI tools from EC-Council’s latest CEH v13 curriculum, enhancing your ethical hacking expertise. These tools are given in the table below.
| AI Tool | Application in Ethical Hacking |
| ShellGPT |
|
| ChatGPT |
|
| FraudGPT |
|
| WormGPT |
|
| DeepExploit |
|
Edoxi’s CEH training empowers professionals to tackle industry-specific cybersecurity challenges with advanced AI tools and technologies. The CEH v13 course is designed for professionals across key industry sectors, including Information Technology, Oil & Gas, Financial Services, Healthcare, E-Commerce, and Government.
Our Certified Ethical Hacking Course empowers you with an understanding of various hacking techniques and methodologies. We, provide you with the ability to think like a hacker while maintaining appropriate ethical standards.
Through a detailed curriculum, hands-on labs, and real-world project scenarios, you will develop a comprehensive AI skill set to perform effective penetration testing, assess the security posture of systems, and mitigate potential attacks.
| Component | Knowledge-Based Exam | Practical Exam (Optional) |
| Exam Code | 312-50 (ECC/VUE) | Via ASPEN iLabs |
| Exam Duration | 4 Hours | 6 Hours |
| Format | 125 multiple-choice question | Hands-on practical assessments |
| Passing Criteria | 60%–85% (varies by question weight) | At least 50% of practicals completed |
| Certification | CEH v13 | CEH Master designation |
| Validity | 3 years | 3 years |
| Recertification | 120 CECs or retake exam | 120 CECs or retake exam |
You will train on EC-Council's iLab platform, where you can practice in secure settings with live networks and real vulnerabilities.
You will learn both attacker and defender strategies to effectively secure systems and mitigate various threats.
You’ll complete structured exercises, including password cracking and exploit testing. You will have access to AI-powered tools for tasks like vulnerability scanning and malware analysis.
Engage in scenarios that mimic actual threats such as advanced persistent threats (APTs), malware attacks, and network breaches. This will help you develop practical cybersecurity skills.
Analyze significant cyberattacks to gain insights into vulnerabilities, attack methods, and response strategies.
You will learn how to identify, analyze, and respond to cybersecurity incidents using advanced tools and methodologies.
Access EC-Council's iLab platform again, with live networks and unpatched systems. This will allow you to perform vulnerability analysis and penetration testing in secure environments.
You will become skilled in using tools like Nmap, Nessus, and Wireshark for network scanning. You can also perform vulnerability assessments using Burp Suite, Acunetix, and OWASP ZAP.
You'll role-play as both attackers and defenders while analyzing historical cyber-attacks to build your skills in threat detection and incident response.
Simulate real-world challenges, including managing SIEM systems and implementing Zero Trust Architecture.
Utilize advanced tools like ShellGPT for penetration testing, FraudGPT for threat detection, and DeepExploit for vulnerability assessment.
Complete real-world projects involving penetration testing, malware analysis, cloud security, IoT assessments, and incident response.
Those managing networks and systems can enhance their ability to detect vulnerabilities and secure IT infrastructure through ethical hacking.
Individuals focused on protecting digital systems can deepen their knowledge of hacking techniques and defensive strategies.
Those entering the IT field can build a strong foundation in cybersecurity and gain a competitive edge with CEH certification.
Professionals from non-IT backgrounds can transition into the growing cybersecurity field by acquiring practical ethical hacking skills.
Developers can learn how to code securely by understanding how attackers exploit software vulnerabilities.
Professionals responsible for assessing system security can benefit from understanding hacking methodologies and risk mitigation.
The CEH v13 course in Dubai offers hands-on labs to help learners gain real-world ethical hacking skills. Our practical training approach ensures a deeper understanding of cybersecurity concepts and better preparation for real-world challenges. Here are some projects and case studies that you will be involved in during the course;
Get access to EC-Council's iLab platform with live networks and unpatched systems. Perform vulnerability analysis and penetration testing in secure, pre-configured environments.
You will simulate real-world cybersecurity challenges, including SIEM systems management and Zero Trust Architecture implementation.
You will master tools like Nmap, Nessus, and Wireshark for network scanning. Perform vulnerability assessments using Burp Suite, Acunetix, and OWASP ZAP.
You get to use advanced tools like ShellGPT for penetration testing, FraudGPT for threat detection, and DeepExploit for vulnerability assessment.
You will complete real-world projects in penetration testing, malware analysis, cloud security, IoT assessments, and incident response.
You will role-play attacker and defender perspectives while analysing historical cyber-attacks. Develop skills in threat detection and incident response.
The Certified Ethical Hacker v13 AI certification unlocks diverse career opportunities in Dubai's thriving technology sector. completing the CEH V13 course opens doors to a wide range of roles in the cybersecurity field, each catering to different interests and skill sets. Here are the key outcomes and career opportunities after the CEH V13 course:

Get expert assistance in getting your CEH v13 Course customised!
Here’s a four-step guide to becoming a certified CEH v13 professional.
Join Edoxi’s CEH v13 Course
At Edoxi, we pride ourselves on being an Award-Winning EC-Council Authorized Training Center, having earned the distinction of EC-Council ATC of the Year for 2023 and 2024. This recognition reflects our unwavering commitment to delivering exceptional cybersecurity education.
With our structured learning approach, expert guidance, and extensive hands-on practice, you can prepare with confidence to succeed in the CEH certification exam. We make sure you have everything you need to excel.
Take advantage of our discounted CEH exam vouchers and special rates for practical certification exams, helping you save significantly as you advance your career.
Experience learning like never before with our advanced cloud labs, where you’ll engage with real-world scenarios, vulnerabilities, and pre-configured security tools that mirror industry standards.
Our courses follow the official EC-Council curriculum and are enhanced by cutting-edge AI tools, practical exercises, and expert instruction. We're here to support you every step of the way.
Join the ranks of over 10,000 professionals we've trained, with a consistent history of success in certifications and career advancement.

Our mentors are leaders and experts in their fields. They can challenge and guide you on your road to success!

Satendra K
Satendra Singh Khari is a renowned cybersecurity expert and the Chief Technology Officer at Edoxi, where he leads the CEH v13 AI program. With over 12 years of experience, he has trained more than 10,000 professionals and earned recognition in the Circle of Excellence for 2023 and 2024. Mr. Khari holds multiple industry certifications, including CISSP, CISM, CEH, CPENT, and CREST, which showcase his expertise in vulnerability assessment, penetration testing, and incident handling.
His practical insights, gained during his tenure as Head of Information Security in Malaysia, enhance the learning experience by providing students with essential technical skills and a clear path to career advancement. Recognized as a leader in his field, he has received the Internet 2.0 Outstanding Leadership Award for three consecutive years (2022-2024), reflecting his dedication to empowering the next generation of cybersecurity professionals.
Here is the list of other major locations where Edoxi offers CEH v13 Certification Course