Edoxi's 40-hour EC-Council-approved Certified Network Defender (CND) v3 course is an industry-leading, vendor-neutral network security certification designed to help you build a successful career in cybersecurity, especially in blue team operations. Whether you are an aspiring cybersecurity professional or an experienced IT practitioner looking to specialise in network defense, this course provides you with the tools, techniques, and strategies to secure modern IT environments.
The course covers core areas such as network security architecture, firewall configuration, IDS/IPS management, secure VPN setup, and risk and vulnerability assessment. You learn to secure complex systems, including cloud infrastructure (AWS, Azure, GCP), IoT devices, mobile platforms, and virtualised environments.
With more than 100 hands-on labs using real-time attack and defense simulations, you gain practical, job-ready skills in configuring networks and implementing layered security measures. The course content follows the “protect, detect, respond, and recover” model, a critical framework for defending enterprise systems from modern cyber threats. This model is depicted below.
4-Pronged Adaptive Security Strategy
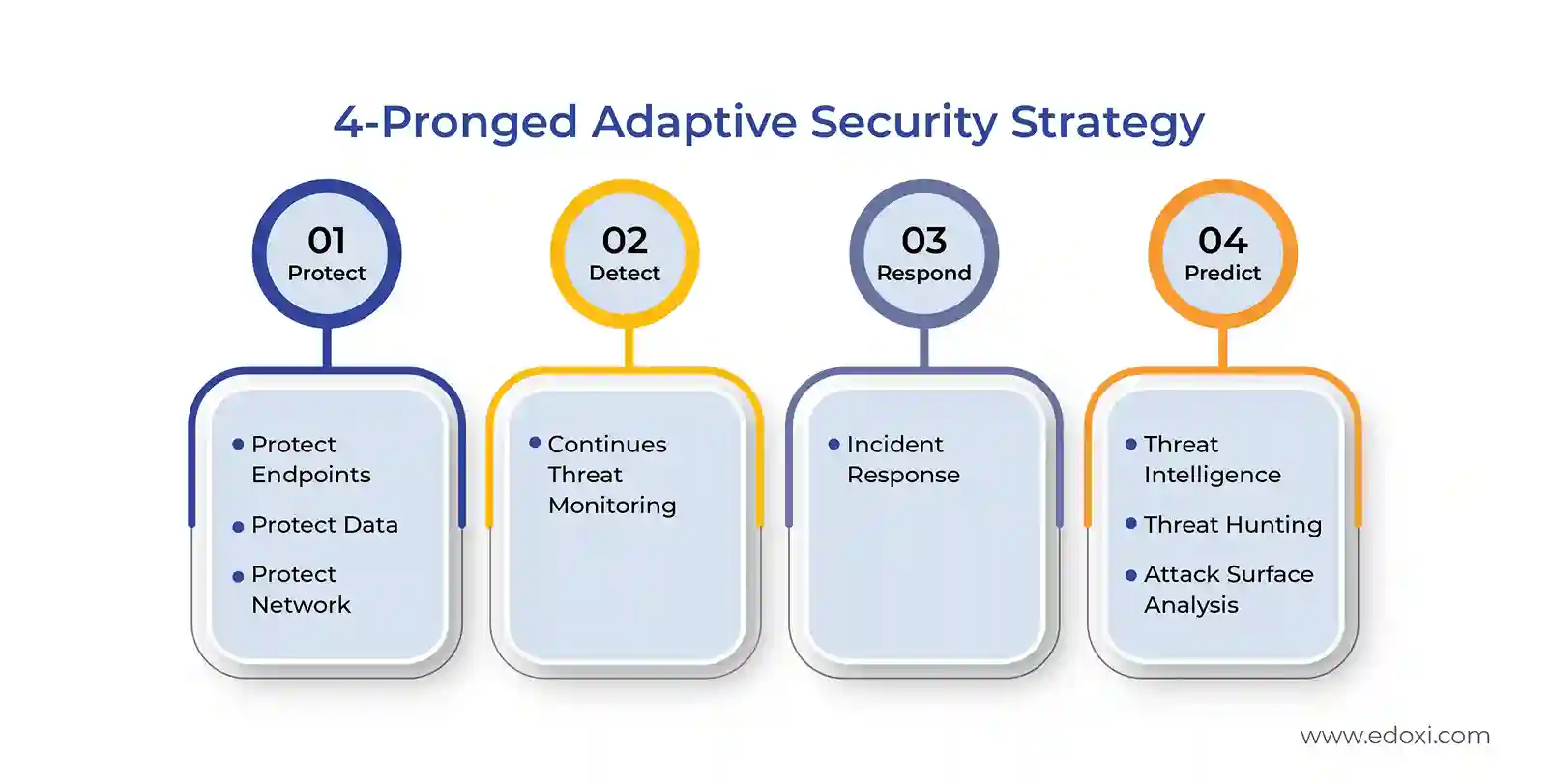
You are trained on live systems using tools such as Suricata, Wazuh, SIEM platforms, and threat intelligence frameworks, ensuring you're equipped to manage real-world challenges in cybersecurity operations. The course also introduces you to security incident response procedures, business continuity planning, and disaster recovery strategies, enabling you to become a complete network defense professional.
Designed in alignment with the official EC-Council Certified Network Defender exam, the training includes structured exam preparation, mock tests, and expert-led guidance to help you clear the certification on your first attempt.
This 40-hour CND online training is available globally through live instructor-led sessions, and includes flexible scheduling for working professionals. With KHDA, EC-Council, CompTIA, and QA QC accreditations, Edoxi ensures high training standards that are recognised worldwide.
Our training includes targeted exam preparation that aligns with the official EC-Council C|ND certification exam, ensuring you're fully prepared to achieve your certification on the first attempt.
| Exam Criteria | Details |
| Exam Name | Certified Network Defender (C|ND) |
| Exam Duration | 4 hours |
| Number of Questions | 100, Multiple Choice |
| Passing Score | 60%-80% (depending on question weightage) |
| Certification Validity | 3 Years |
| Exam Administration Authority | EC-Council |
Once you pass the exam, you become a Certified Network Defender. The CND certification is highly regarded by employers in sectors such as banking, government, healthcare, telecom, IT services, and defense, making it an ideal qualification to improve your career prospects or transition into cybersecurity roles such as Network Security Analyst, Security Operations Center (SOC) Analyst, Incident Responder, or Cybersecurity Specialist.
Start your journey toward becoming a certified network defender and advance your career in one of the world’s most in-demand industries.
You get to practise in a cloud-based lab environment built specifically for hands-on cybersecurity training, giving you real-world experience.
You have access to up-to-date study materials directly from EC-Council, covering all the latest concepts in network defense.
You can take part in exercises tailored to real job roles in cybersecurity, helping you build relevant, practical skills for your career.
You experience how to detect and respond to simulated network, host, and application-based attacks using industry-standard tools.
You get hands-on with firewall, IDS, and IPS tools like pfSense, Suricata, and Wazuh during practical lab workshops.
You learn to identify indicators of compromise, assess attack surfaces, and engage in threat hunting exercises.
All those who manage network infrastructure, this course helps you secure it effectively.
Security Analysts and SOC Operators who want to learn to detect threats, monitor networks, and implement defensive measures with confidence.
Expand your skills by adding advanced network defense techniques to your expertise.
Gain the defensive security skills you need to move into specialized cybersecurity roles.
If you already understand the basics of cybersecurity, this course will help you specialise in network defense.
Strengthen your ability to develop and enforce effective network security policies.
Our Hands-on Labs and practical sessions strengthen your cyber defense skills in a cloud-based environment. You gain real-world experience through tactical exercises, role-based training, and case studies powered by EC-Council’s accredited cybersecurity lab. Our CND course includes over 100 practical labs covering the following key activities:
You simulate network, application, and host-based attacks to understand how cyber threats work. Then, you apply effective defense strategies and deploy countermeasures to protect systems from those attacks.
You learn how to configure identity and access controls, set up security policies, manage assets, and implement cryptography, VPNs, and network segmentation to strengthen your network defenses.
You learn how to deploy firewalls and set up intrusion detection and prevention systems using tools like pfSense, Suricata, and Wazuh to guard your network perimeters effectively.
You learn how to secure Windows, Linux, mobile, and IoT devices by performing OS hardening, managing patches, applying encryption, conducting file integrity checks, and adjusting permission settings.
You learn how to apply security controls to virtual machines, containers, and cloud platforms by setting up IAM, KMS, and secure storage and network configurations on AWS, Azure, and GCP.
You learn how to secure wireless communications by configuring routers, enabling Wi-Fi encryption, and implementing strong authentication methods.
You learn how to capture and analyze network traffic with Wireshark, identifying anomalies through detailed log and packet analysis.
You learn how to create and execute incident response plans, perform forensic investigations, and simulate disaster recovery to ensure ongoing business operations.
You learn how to conduct threat hunting, examine IOCs, IOAs, and IOEs, and develop predictive models to detect and prevent future attacks.
Our CND Course builds your expertise in network defense and takes a proactive role in protecting digital infrastructures. Through this course, you gain hands-on skills and industry-recognised knowledge that prepares you for high-demand cybersecurity roles worldwide. Here are the Major Course Outcomes:

Get expert assistance in getting your Certified Network Defender Course customised!
Here’s a four-step guide to becoming a certified Certified Network Defender professional.
Join Edoxi’s Certified Network Defender Course
Take the next step in your cybersecurity career with expert-led training designed to get you certified and ready to pursue further career. At Edoxi, you learn in a hands-on, cloud-based environment that mirrors real-world network defense scenarios. Here are the key reasons to choose Edoxi.
You have the opportunity to train with an EC-Council-authorised partner recognised for excellence in cybersecurity education across the UAE.
You can master exam concepts through structured lessons, expert-led sessions, and hands-on lab practice tailored to exam success.
You get to work in EC-Council’s cloud lab, where you explore live network infrastructure, simulate attacks, and apply real-time defense tools.
You get full access to official courseware, extra practice resources, and one-on-one mentoring from seasoned cybersecurity trainers.
You can join a growing network of certified professionals who were trained at Edoxi and now thrive in top security roles worldwide.
You can build a future-ready career by continuing your journey with advanced EC-Council certifications like CEH, CHFI, and ECSS.

Our mentors are leaders and experts in their fields. They can challenge and guide you on your road to success!

Satendra K
Satendra Singh Khari is a renowned cybersecurity expert and the Chief Technology Officer at Edoxi, where he leads the CEH v13 AI program. With over 12 years of experience, he has trained more than 10,000 professionals and earned recognition in the Circle of Excellence for 2023 and 2024. Mr. Khari holds multiple industry certifications, including CISSP, CISM, CEH, CPENT, and CREST, which showcase his expertise in vulnerability assessment, penetration testing, and incident handling.
His practical insights, gained during his tenure as Head of Information Security in Malaysia, enhance the learning experience by providing students with essential technical skills and a clear path to career advancement. Recognized as a leader in his field, he has received the Internet 2.0 Outstanding Leadership Award for three consecutive years (2022-2024), reflecting his dedication to empowering the next generation of cybersecurity professionals.
Here is the list of other major locations where Edoxi offers Certified Network Defender (CND) Course
You need a basic understanding of networking concepts like TCP/IP, routing, and switching. This foundation helps you grasp core defensive strategies more effectively during the course.
C|ND is a globally recognised certification that validates your network defense skills. With this credential, you can confidently apply for roles such as Network Security Administrator, SOC Analyst, or Cybersecurity Engineer.
C|ND focuses purely on defensive security. Unlike offensive certifications, it prepares you to detect, prevent, and respond to cyber threats. This certification is ideal for professionals focused on network protection.
You face 100 multiple-choice questions in 4 hours. The passing score ranges from 60% to 80% based on question difficulty. Once certified, your C|ND credential stays valid for three years.
Yes, we offer a customized 5-day corporate training program. Your team trains in simulated network environments tailored to your company’s security infrastructure and defense needs.