Edoxi's 40-hour online CompTIA CySA+ certification training focuses on advanced cybersecurity threat detection and response. It is designed for professionals looking to expand their security analysis skills. You learn to identify, analyse, and respond to complex security incidents in various environments.
The CompTIA CySA+ training includes extensive practical sessions that simulate real-world cybersecurity scenarios. You can engage with professional tools such as Splunk, ELK Stack, and Wireshark to analyse real security events. These sessions help you gain direct experience with tools used in the industry.
You can also work through vulnerability management lifecycles, malware traffic analysis, and threat hunting exercises. These tasks reflect the daily responsibilities of a security operations centre (SOC). This hands-on approach ensures graduates can confidently apply their skills in professional environments. You develop the expertise needed for mid-level cybersecurity roles. The skills gained are relevant across sectors such as finance, healthcare, and government. Our CompTIA CySA+ training focuses on practical competencies that are highly valued by employers worldwide.
Upon completion, you possess expertise for mid-level cybersecurity roles, validated by an Edoxi training certificate. Our CompTIA CySA+ curriculum covers all four CompTIA CySA+ domains. It prepares you for the CS0-003 certification exam through targeted training and hands-on practice. This CompTIA CySA+ certification strengthens your credentials, enhancing career prospects across finance, healthcare, and government sectors. Enrol now to advance your career in cybersecurity analysis.
Master industry-standard tools including Splunk, ELK Stack, Wireshark, and vulnerability scanners through guided practical exercises.
Analyze authentic security incidents and vulnerabilities mirroring actual enterprise environments and attack vectors.
Access authorized CompTIA study guides, lab manuals, and specialized resources for exam preparation and reference.
Receive targeted coaching for the CS0-003 exam with practice questions, domain-specific reviews, and proven test-taking strategies.
Working in cybersecurity roles seeking to advance their threat analysis capabilities.
Managing network infrastructure with basic security knowledge, ready for specialized training.
Responsible for system security, wanting to develop advanced threat detection skills.
Looking to enhance their technical capabilities and advance to mid-level SOC positions.
Providing security services that need formal certification and analytical methodology training.
With networking knowledge transitioning to specialized cybersecurity analysis roles.
The course features extensive hands-on labs using professional security tools such as Splunk, ELK Stack, Wireshark, and vulnerability scanners. You will work on real-world SOC projects. Some of the key projects include:
Analyze security logs from multiple sources to identify suspicious behaviors, establish patterns, and generate comprehensive incident reports with mitigation recommendations.
Conduct vulnerability assessments in a simulated enterprise environment, prioritize findings using CVSS, and develop complete remediation plans with proper documentation.
Perform active and passive threat hunting using advanced tools to detect indicators of compromise and document findings according to industry standards.
Use Wireshark, REMnux, and PacketTotal to capture, analyze, and document malicious network traffic patterns, extracting key indicators for threat intelligence.
Implement monitoring solutions to identify suspicious DNS queries and web requests, distinguishing between normal activity and potential command-and-control communications.
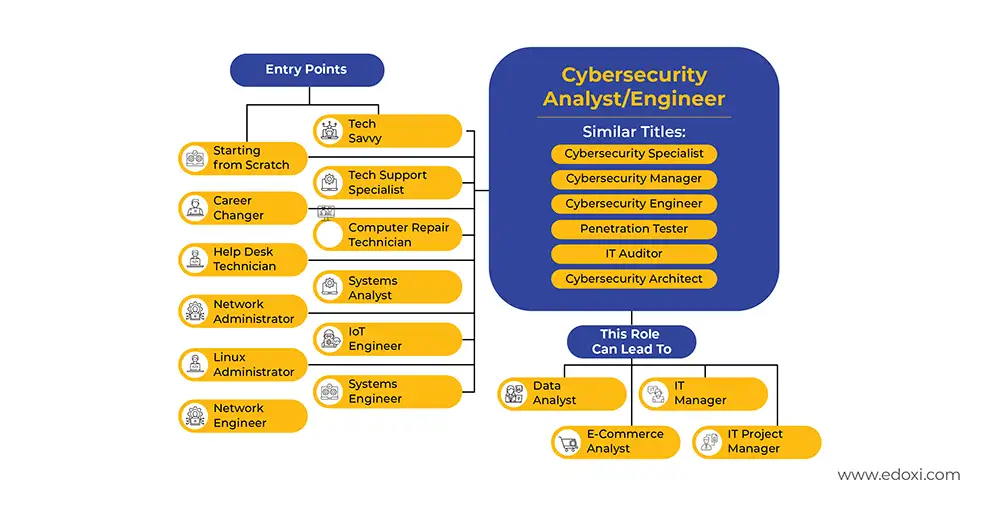
Earning the CompTIA CySA+ certification opens clear career paths in cybersecurity threat detection and analysis, with strong growth opportunities. The course outcomes include:

Get expert assistance in getting you CompTIA Cybersecurity Analyst (CySA+) Course customised!
Here’s a four-step guide to becoming a certified CompTIA CySA+ professional.
Join Edoxi’s CompTIA Cybersecurity Analyst (CySA+) Course
With numerous options out there, Edoxi proves to be the best. The following are the reasons why Edoxi’s CompTIA CySA+ training is the ideal option for you:
Our official CompTIA partnership ensures curriculum alignment with CySA+ certification requirements and access to authorized study materials.
Our instructors bring practical SOC, vulnerability management, and incident response experience directly to the classroom environment.
Students train in specialized facilities equipped with enterprise-grade security tools that mirror professional working environments.
Multiple course timing options accommodate working professionals without compromising their current career responsibilities.
We deliver corporate training to government bodies, banks, and enterprises in the Middle East and globally, customised for organisational requirements.
Edoxi delivers Cybersecurity training across GCC nations, including the UAE, Saudi Arabia, Qatar, Oman, and is expanding successfully into European markets.

Our mentors are leaders and experts in their fields. They can challenge and guide you on your road to success!

Maria Mehwish
Maria Mehwish is a forward-thinking and knowledgeable information security leader with a strong background in building, updating, and maintaining digital protections for various organisations. As a certified CEH, CCSP, CCT, and CISSP Trainer, Maria has a proven track record of delivering innovative and immersive coursework, enhancing learning experiences for cyber threats, ethical hacking, security policy, DevSecOps, and cloud security. With excellent verbal and written communication skills, she is also adept at troubleshooting problems and building successful solutions.
Maria is a self-motivated individual with a strong sense of personal responsibility, capable of managing projects from start to finish. Her expertise in Amazon Web Services, Java/Go/Python/C++, DevSecOps, computer security, Linux, penetration testing, and risk analysis, among others, makes her a valuable asset to any organisation. Maria, a British national, is a native English speaker and has intermediate proficiency in Urdu.
Here is the list of other major locations where Edoxi offers CompTIA Cybersecurity Analyst (CySA+) Course