Edoxi’s 40-hour CompTIA PenTest+ (PT0-003) online training equips you with practical skills to identify, exploit, and document vulnerabilities across networks, systems, and applications. This 5-day program blends essential theory with real-world practice, making it ideal for cybersecurity professionals, network engineers, and IT managers. Our hands-on labs let you practice real-world hacking tests using popular penetration testing tools such as Kali Linux, Metasploit, and Nmap, to build job-ready skills.
Our CompTIA PenTest+ training is fully aligned with the PT0-003 exam objectives and helps you prepare confidently for the PenTest+ certification exam. It covers key areas such as reconnaissance, vulnerability scanning, exploitation, post-exploitation, and reporting. You will develop technical proficiency through immersive labs and guided projects that reflect real offensive security challenges.
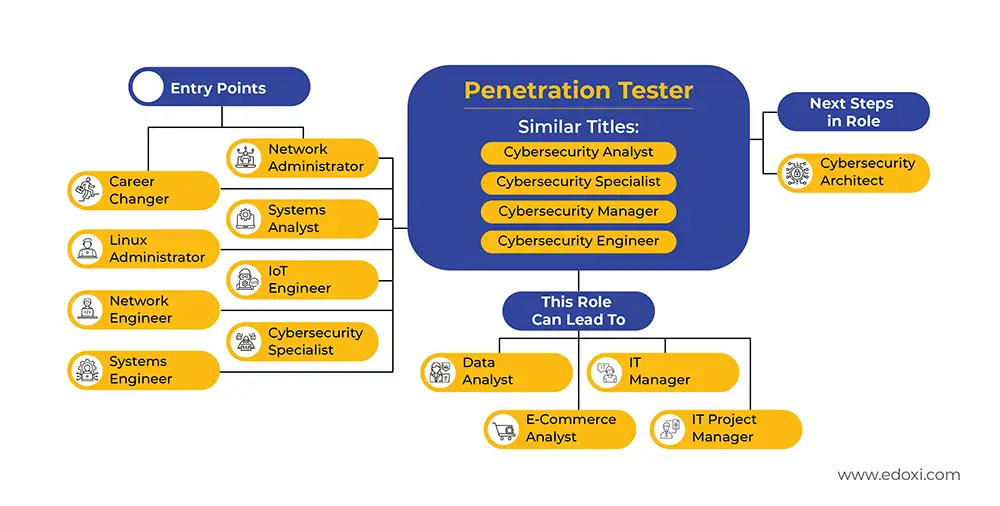
The course serves as a gateway to advanced cybersecurity roles. Upon successful completion of the PenTest+ training, you will receive Edoxi’s CompTIA PenTest+ course completion certificate. With the certificate, your skills in penetration testing and vulnerability assessment will be validated for various cybersecurity roles.
Enrol now to advance your career in cybersecurity and gain globally recognised credentials that open doors to high-demand roles in ethical hacking and offensive security.
CompTIA PenTest+ Certification (PT0-003) Exam Details
The CompTIA PenTest+ (PT0-003) exam tests your ability to perform penetration testing, identify and assess vulnerabilities, and conduct security assessments in diverse environments. Below is a breakdown of the key exam details:
| Exam Criteria | Details |
| Exam Code | PT0-003 |
| Exam Name | CompTIA PenTest+ Certification |
| Duration | 165 minutes |
| Number of Questions | 90, Multiple Choice |
| Passing Score | 750/1000 |
| Certification Validity | 3 years |
| Exam Administration Authority | Pearson VUE |
Practice in realistic environments using professional tools like Kali Linux, Metasploit, and Burp Suite.
Receive targeted review sessions, practice tests aligned with PT0-003
Access comprehensive guides, practice exams, tool usage handbooks, and script samples for exam preparation.
Experience real-time attack and defense scenarios through competitive team-based activities.
Solve capture-the-flag exercises that simulate identifying and exploiting security vulnerabilities in virtual machines.
Master comparative analysis using tools like Nessus, OpenVAS, and Nikto while identifying false positives.
Working in security operations, incident response, or vulnerability management.
Responsible for implementing and securing the network infrastructure.
Overseeing security operations and vulnerability management programs.
Providing security assessments and recommendations to clients.
Performing authorized security testing of systems and applications.
Looking to advance their security credentials and specialization.
Our CompTIA PenTest+ course features hands-on projects like enterprise network pentests, web app exploits, and Active Directory attacks. You’ll also perform Wi-Fi hacking, phishing simulations, and password cracking using real-world tools. Key practical activities include:
Conduct an end-to-end penetration test including reconnaissance, scanning, exploitation, and professional reporting on a complex simulated corporate environment.
Identify and exploit OWASP Top 10 vulnerabilities in test web applications using tools like OWASP ZAP and Burp Suite.
Compromise weak credentials and escalate privileges in a Windows domain environment using tools like BloodHound and Mimikatz.
Perform practical Wi-Fi security assessments including WPA2 cracking and man-in-the-middle attacks using Aircrack-ng and Wireshark.
Design and execute controlled phishing campaigns to demonstrate human vulnerabilities using Gophish and Social Engineering Toolkit.
Apply dictionary and brute force attacks against password hashes using John the Ripper, Hashcat, and Hydra.
The CompTIA PenTest+ proves your skills in penetration testing and finding security risks. It teaches you how to simulate attacks and suggest fixes. CompTIA PenTest+ certification helps you get well-paying cybersecurity jobs with good growth opportunities. Additional key outcomes include:

Get expert assistance in getting you CompTIA PenTest+ Course customised!
Here’s a five-step guide to becoming a certified CompTIA PenTest+ professional.
Join Edoxi’s CompTIA PenTest+ Course
Among many available options, Edoxi stands out as a top choice. The following are the reasons why Edoxi’s CompTIA Pentest+ training is the ideal option for you:
Our official CompTIA partnership ensures curriculum alignment with PenTest+ certification requirements and access to exclusive exam preparation resources.
Our trainers bring extensive penetration testing experience from banking, telecommunications, and government security operations to the classroom.
Practice with industry-standard tools like Kali Linux, Metasploit, and Burp Suite in labs simulating real-world vulnerable environments.
We structure training to build your cybersecurity credentials progressively, mapping your journey from foundational to advanced specialized certifications.
Our small batch sizes ensure individualized attention during complex penetration testing exercises with detailed feedback on your techniques.
We've delivered specialized penetration testing training to major organizations customizing programs for specific security requirements.

Our mentors are leaders and experts in their fields. They can challenge and guide you on your road to success!

Maria Mehwish
Maria Mehwish is a forward-thinking and knowledgeable information security leader with a strong background in building, updating, and maintaining digital protections for various organisations. As a certified CEH, CCSP, CCT, and CISSP Trainer, Maria has a proven track record of delivering innovative and immersive coursework, enhancing learning experiences for cyber threats, ethical hacking, security policy, DevSecOps, and cloud security. With excellent verbal and written communication skills, she is also adept at troubleshooting problems and building successful solutions.
Maria is a self-motivated individual with a strong sense of personal responsibility, capable of managing projects from start to finish. Her expertise in Amazon Web Services, Java/Go/Python/C++, DevSecOps, computer security, Linux, penetration testing, and risk analysis, among others, makes her a valuable asset to any organisation. Maria, a British national, is a native English speaker and has intermediate proficiency in Urdu.
Here is the list of other major locations where Edoxi offers CompTIA PenTest+ Course
Professionals with the PenTest+ certification earn an average of $116,000 as Penetration Testers, $72,500 as Vulnerability Analysts, and $90,000 as Threat Intelligence Analysts. Salaries rise with experience, making PenTest+ a strong launchpad for advanced cybersecurity roles.