Edoxi’s 35-hour Computer Hacking Forensic Investigator (CHFI) Certification Course is designed for cybersecurity professionals, IT specialists, and law enforcement officers seeking advanced expertise in digital forensics and cybercrime investigation. Delivered by the best training institute for CHFI training in Kuwait, Edoxi provides in-depth knowledge of computer forensics methodologies, digital evidence handling, and incident response aligned with global investigation standards.
Our CHFI training in Kuwait combines instructor-led sessions with hands-on lab exercises using professional forensic tools such as Autopsy, FTK Imager, and Redline. You practice real-world scenarios on Windows, Linux, and Mac systems, developing expertise in data recovery, forensic imaging, malware analysis, and evidence preservation. These exercises ensure skills are directly applicable to practical investigations and legal proceedings.
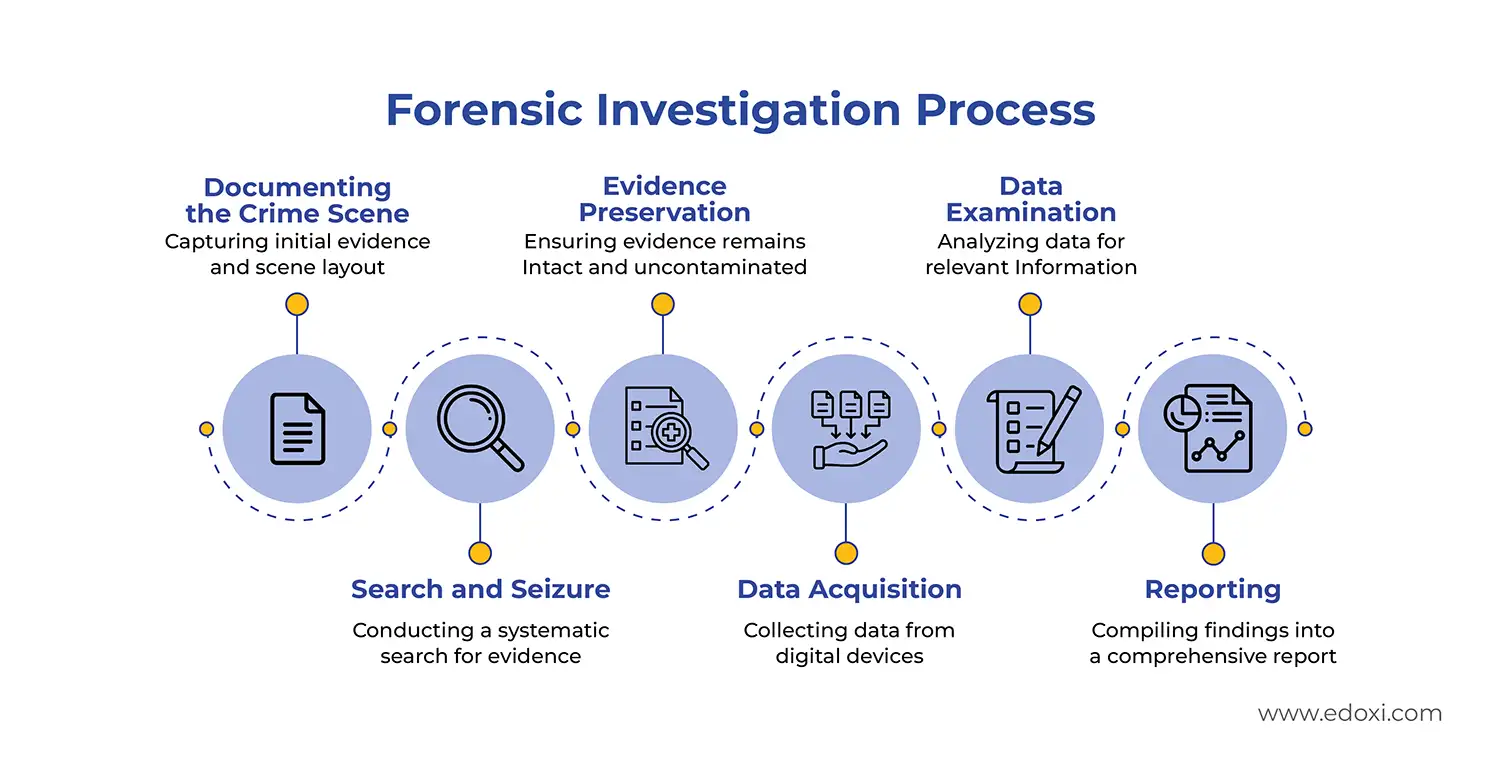
The image below outlines the CHFI certification course, featuring a curriculum focused on malware, cloud, and mobile forensics, alongside an infographic detailing the six-stage Forensic Investigation Process: from crime scene documentation and evidence preservation to data examination and final reporting.
The program also includes preparation for the EC-Council Computer Hacking Forensic Investigator (CHFI) exam, including a mock test to assess readiness and strengthen performance. Here are the key exam details of the CHFI Course:
Upon successful completion of CHFI classes, you are fully equipped to conduct forensic examinations. Exam Details
| Exam Criteria | Details |
| Exam Code | 312-49 |
| Exam Name | Computer Hacking Forensic Investigator |
| Duration | 4 hours |
| Passing Score | 60% |
| Certification Validity | 3 years |
| Recertification | Retake the exam before expiration |
| Exam Administration Authority | EC-Council |
This certification helps you analyse digital evidence, prepare court-admissible reports, and provide expert testimony.
Our course enables professionals to apply digital forensic techniques across multiple industries to investigate incidents, strengthen security, support legal processes, and manage cyber risks effectively.
Computer Hacking Forensic Investigator Course Applications Across Industries
| Domains | Practical Applications |
| Cybersecurity | Analyse cyber threats using forensic techniques, and strengthen security incident response frameworks |
| Law Enforcement | Conduct cybercrime investigations, preserve and analyse digital evidence for legal cases |
| Legal Compliance | Ensure adherence to data protection laws (GDPR, CCPA), and investigate regulatory non-compliance issues |
| Digital Forensics | Recover and analyse forensic evidence from compromised systems, detect and neutralise malware threats |
| IT Security | Investigate internal and external security breaches, and strengthen IT security policies with forensic insights |
| Corporate Risk Management | Identify cybersecurity risks affecting corporate operations, and implement forensic-based risk mitigation strategies |
Edoxi also offers corporate training for organisations, with customised delivery models designed to meet the specific requirements of enterprises and governments in cybersecurity. The CHFI course fee is competitively structured, offering excellent value through expert-led instruction, hands-on labs, and an internationally recognised certification.
Gain hands-on experience with industry-standard forensic tools such as Autopsy, FTK Imager, and Redline, helping you conduct professional digital investigations with confidence.
Perform forensic examinations across Windows, Linux, and macOS operating systems, allowing you to broaden your investigation capabilities.
Build practical skills in recovering deleted data, analysing file systems, and extracting critical digital evidence, enabling you to handle real investigation scenarios.
Develop expertise in hex editing with the HxD tool and carry out binary, decimal, and hexadecimal data conversions to support your in-depth data examination.
Learn accurate documentation methods, maintain proper chain of custody, and prepare court-admissible forensic reports that strengthen your professional credibility.
Assess your exam readiness through a CHFI mock test and approach the certification exam with greater confidence.
IT security specialists and analysts who want to expand their skills into digital forensics and evidence collection.
Police officers, detectives, and investigators involved in handling digital evidence and investigating cybercrimes.
Network and security professionals aiming to strengthen incident response through forensic investigation skills.
Lawyers, legal consultants, and paralegals who work on cybercrime cases and need knowledge of digital evidence procedures.
Professionals responsible for regulatory compliance and internal security breach investigations.
Enterprise security professionals looking to develop in-house capabilities for incident response and cyber investigations.
Our CHFI course in Kuwait offers hands-on learning in a fully equipped lab, letting you investigate cybercrimes, collect digital evidence, and analyse data on Windows, Linux, and Mac systems. Here are the lab activities:
In this activity, you perform forensic investigations on Windows, Linux, and Mac systems. Learn techniques to extract, preserve, and analyse digital evidence from each environment.
During this activity, you use HxD and other forensic tools to edit hexadecimal data. Develop skills for recovering deleted or corrupted files through low-level analysis.
In this activity, you convert binary, decimal, and hexadecimal values accurately. Gain expertise in interpreting raw data for forensic investigations.
During this activity, you create forensic disk images and recover data from compromised storage devices. Learn to maintain data integrity while performing analysis for investigative purposes.
Completing Edoxi’s AutoCAD MEP Training Course in Kuwait equips you with job-ready skills for designing, coordinating, and managing MEP systems in modern construction projects. Here are the major learning outcomes you can expect from the course:

Get expert assistance in getting your CHFI Course customised!
Here’s a four-step guide to becoming a certified CHFI professional.
Join Edoxi’s CHFI Course
Among many available options, Edoxi stands out as a top choice. The following are the reasons why Edoxi’s CHFI classes in Kuwait are an ideal option for you:
Recognised as EC-Council ATC of the Year for 2023 and 2024, showcasing our excellence in cybersecurity and digital forensics education.
We have delivered CHFI and cybersecurity training to government entities and leading companies in the MENA region, including UAE Federal Government, Saudi Aramco, Reserve Bank of Zimbabwe, and more.
Benefit from discounted CHFI exam vouchers and special rates for the practical certification exam.
Practice in advanced cloud labs featuring real-world scenarios, vulnerabilities, and pre-configured forensic and security tools.
Follow EC-Council’s official curriculum, hands-on exercises, and expert instruction to build practical skills.
Over 10,000 professionals trained with consistent success in certification achievements and career advancement.

Our mentors are leaders and experts in their fields. They can challenge and guide you on your road to success!

Satendra K
Satendra Singh Khari is a renowned cybersecurity expert and the Chief Technology Officer at Edoxi, where he leads the CEH v13 AI program. With over 12 years of experience, he has trained more than 10,000 professionals and earned recognition in the Circle of Excellence for 2023 and 2024. Mr. Khari holds multiple industry certifications, including CISSP, CISM, CEH, CPENT, and CREST, which showcase his expertise in vulnerability assessment, penetration testing, and incident handling.
His practical insights, gained during his tenure as Head of Information Security in Malaysia, enhance the learning experience by providing students with essential technical skills and a clear path to career advancement. Recognized as a leader in his field, he has received the Internet 2.0 Outstanding Leadership Award for three consecutive years (2022-2024), reflecting his dedication to empowering the next generation of cybersecurity professionals.
Here is the list of other major locations where Edoxi offers CHFI Course